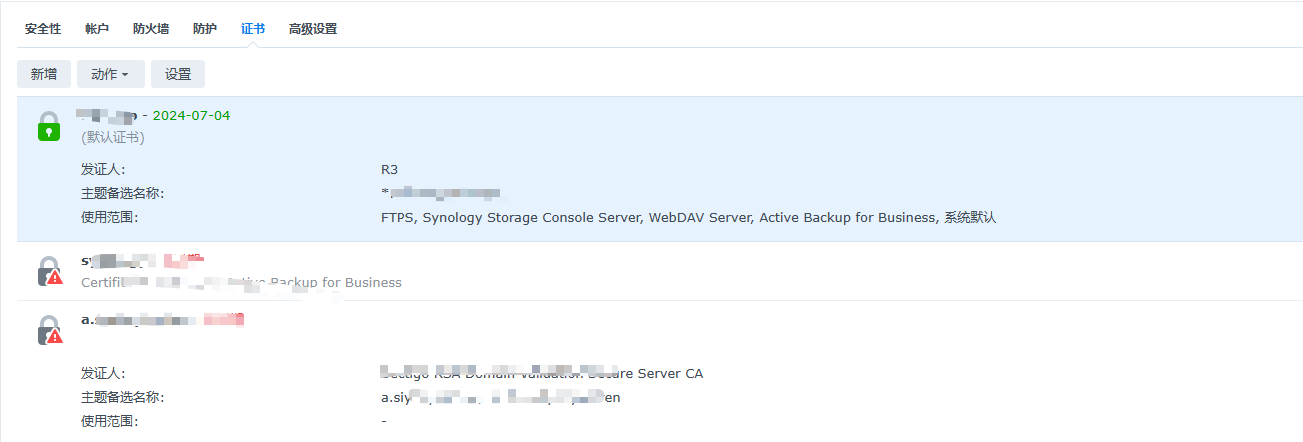
群晖默认证书过期
安全性风险: 默认证书过期后,HTTPS连接可能会受到影响,用户的数据传输可能会变得不安全,因为证书的过期可能会导致信息被窃听或篡改的风险增加。
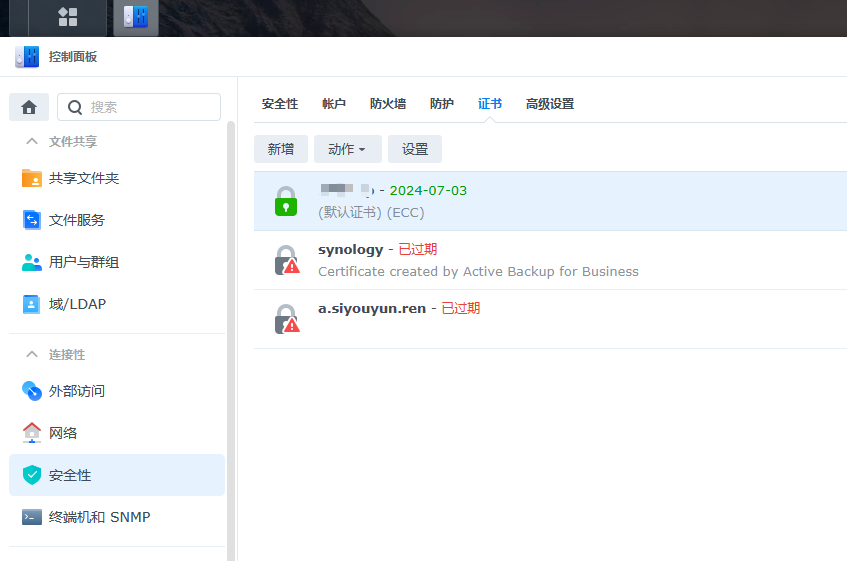
Docker安装acme.sh容器
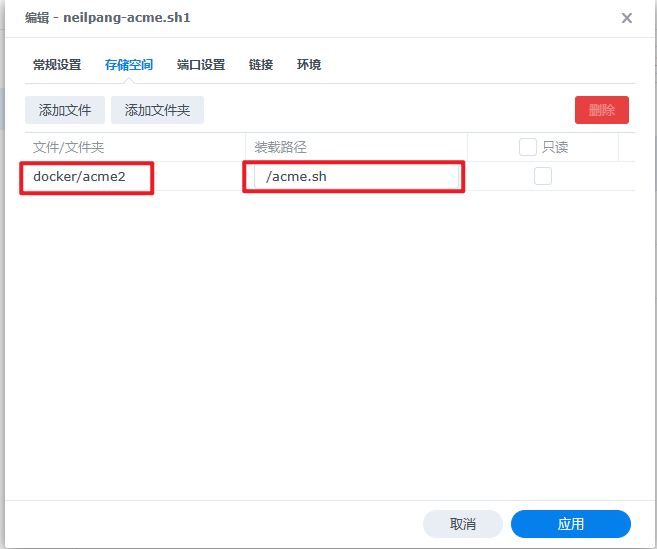
在共享文件里新建acme目录
拉取镜像
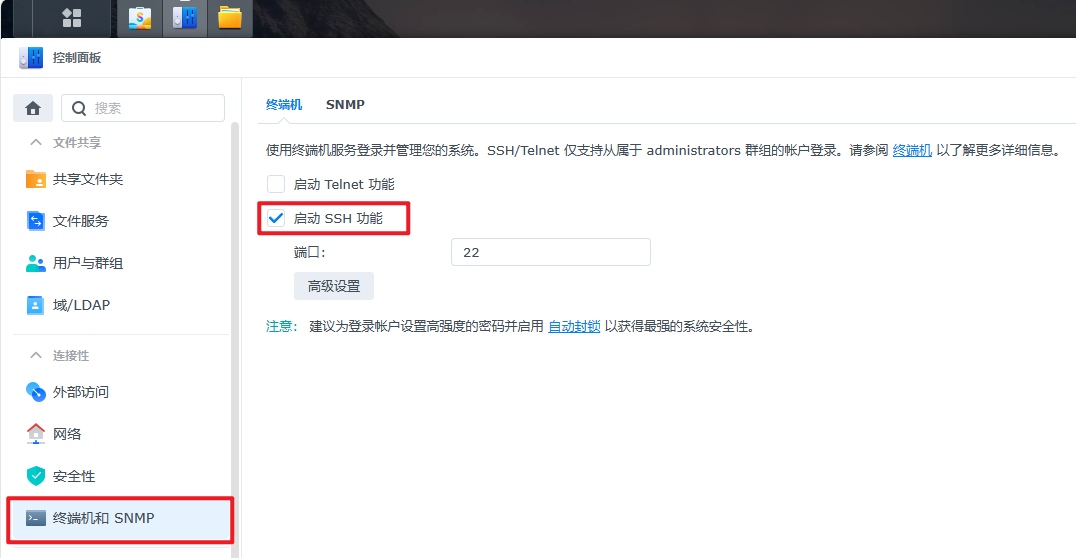
打开群晖 SSH 功能
使用Xshell 工具登录群晖命令行管理界面
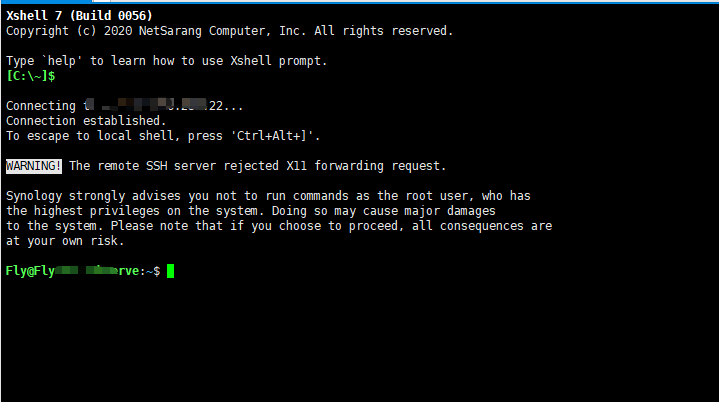
$ 符号是没有管理员权限的,在全面输入
sudo su使用管理员密码登录


拉取 neilpang/acme.sh 镜像
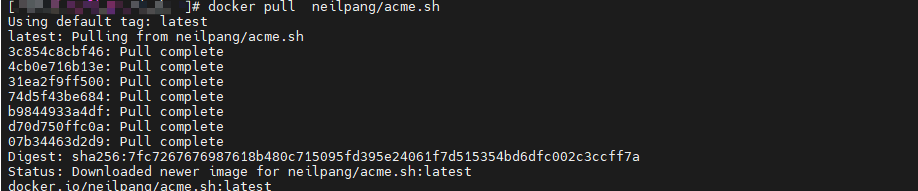
镜像拉取完毕去群晖图像界面
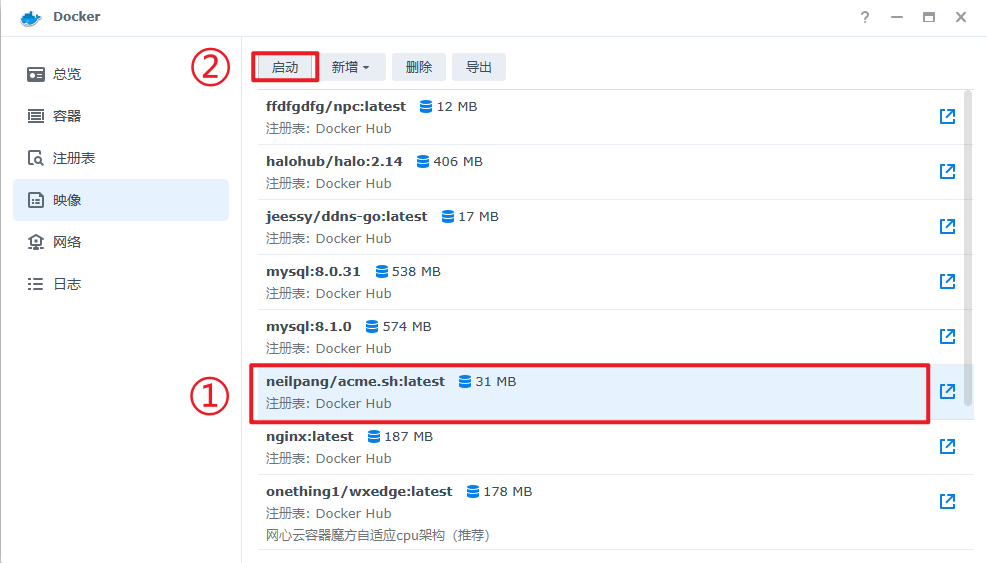
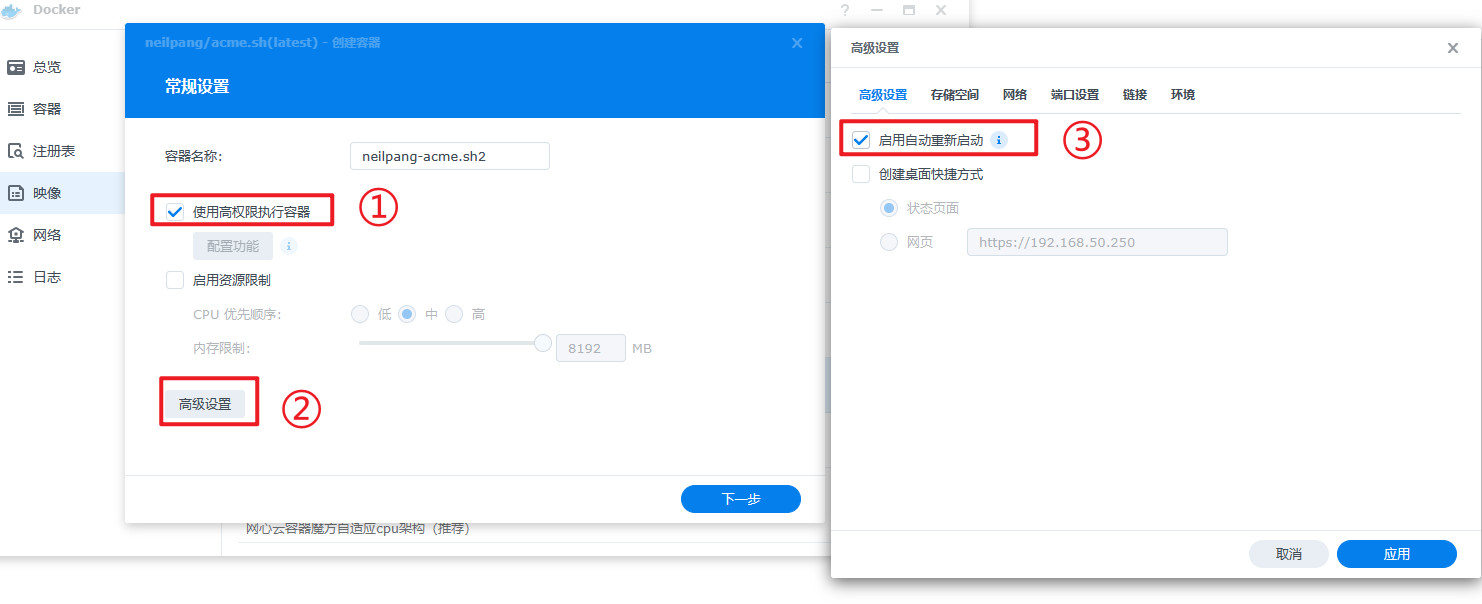
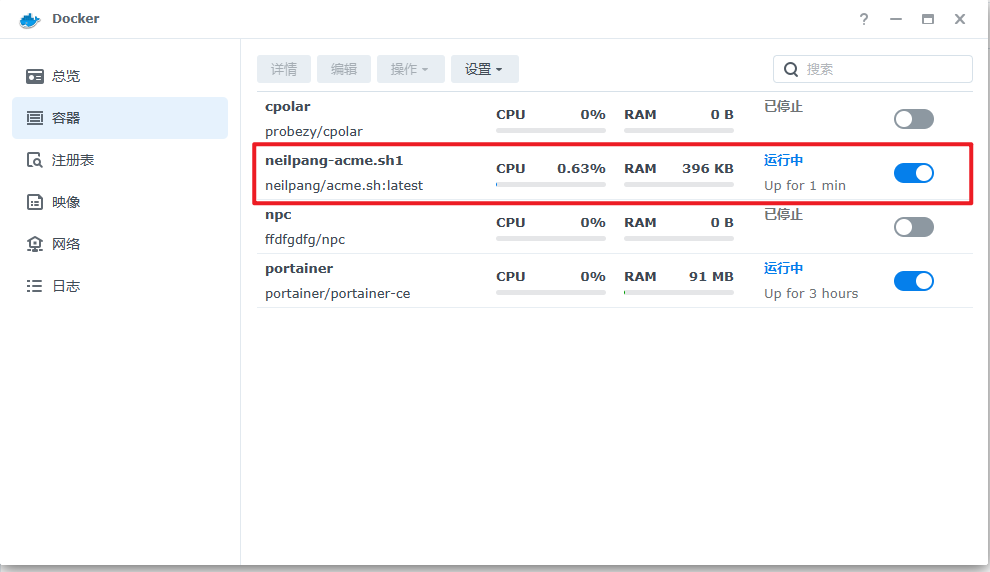
安装neilpang/acme.sh 镜像

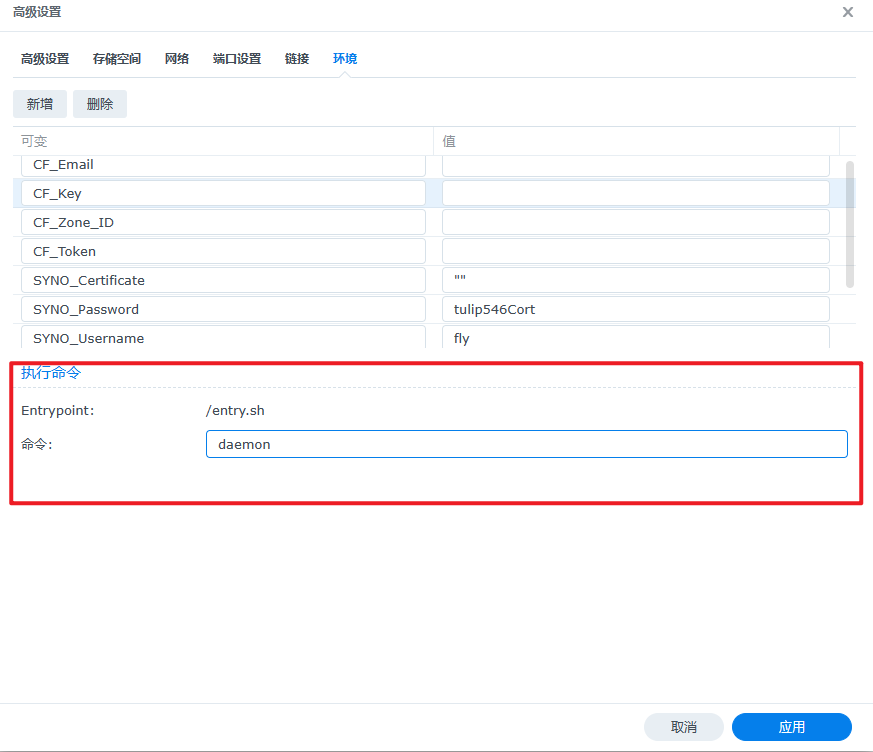
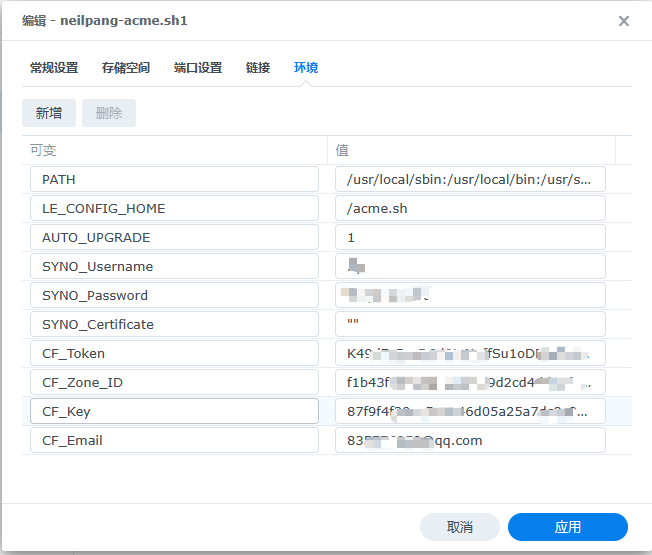
添加环境变量
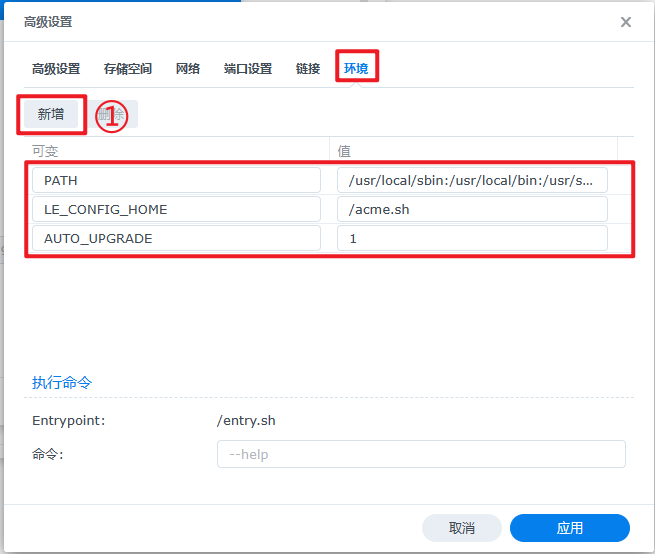
添加环境变量
需要部署群晖的参数
SYNO_Username:群晖管理员账号
SYNO_Password:群晖管理员登录密码
SYNO_Certificate:"" (证书名,给空字符即可)
更多参数可参考Github上的说明
Synology NAS Guide · acmesh-official/acme.sh Wiki · GitHub
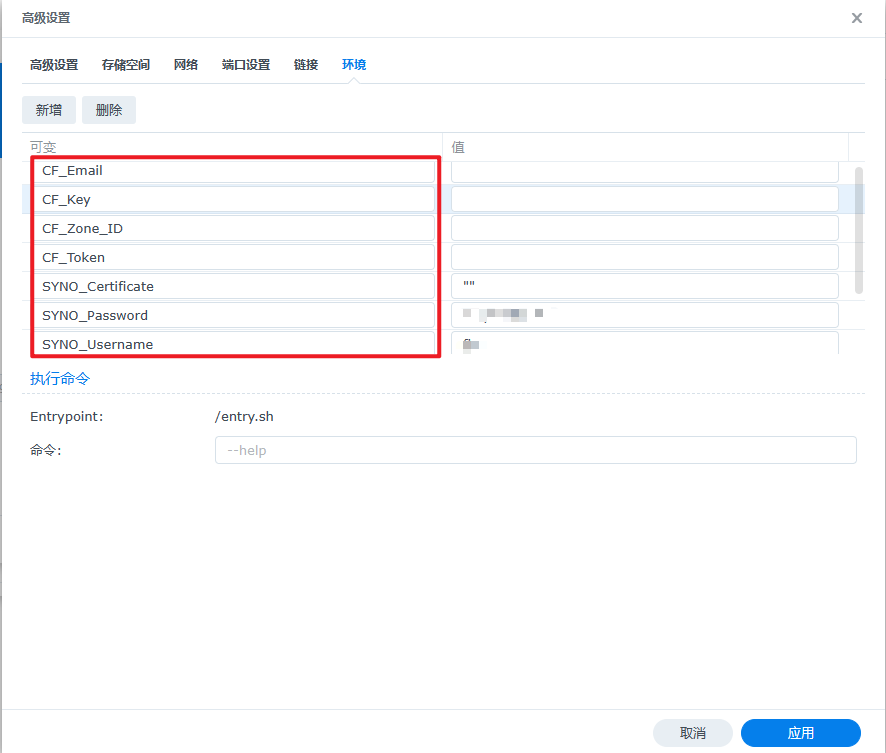
需要申请证书的域名参数
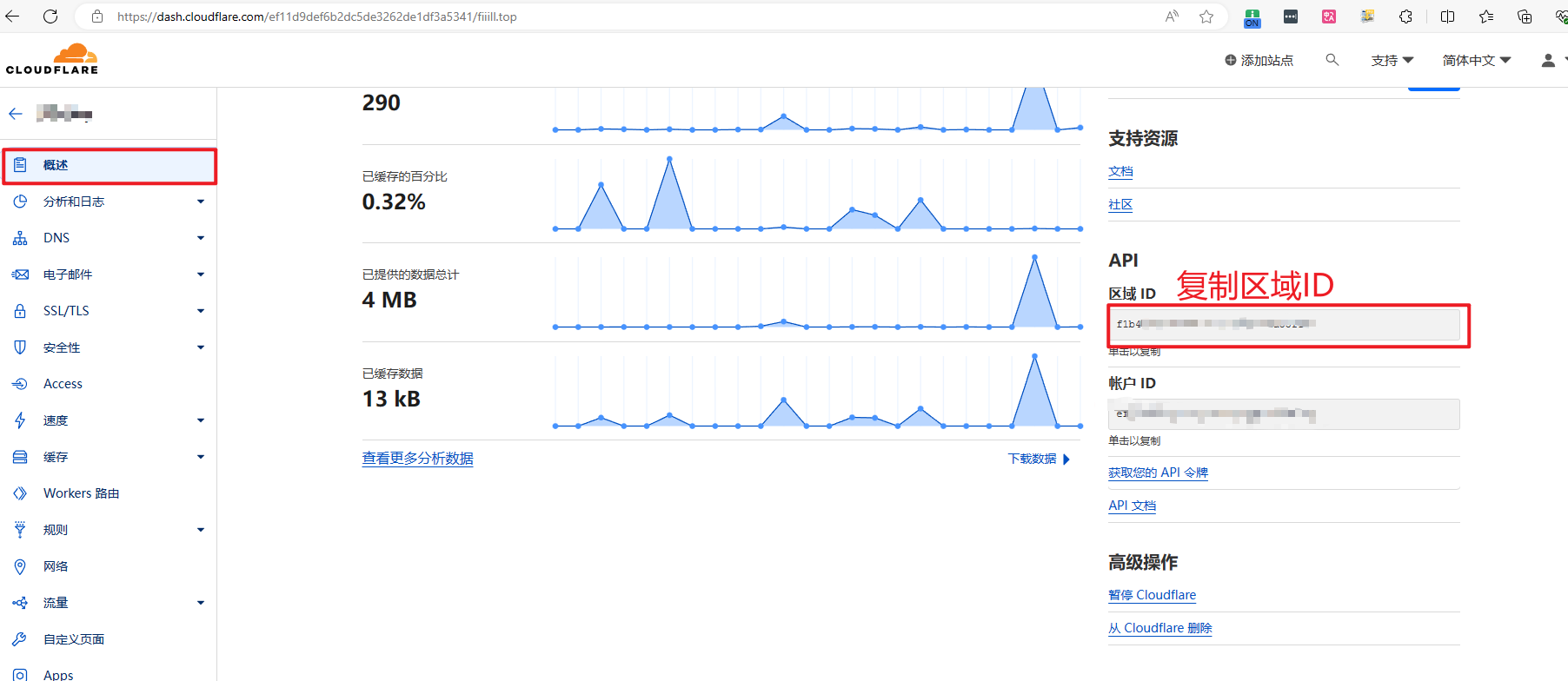
CF_Zone_ID: 登录Cloudflare之后,进入域名管理在“概述”右下角上
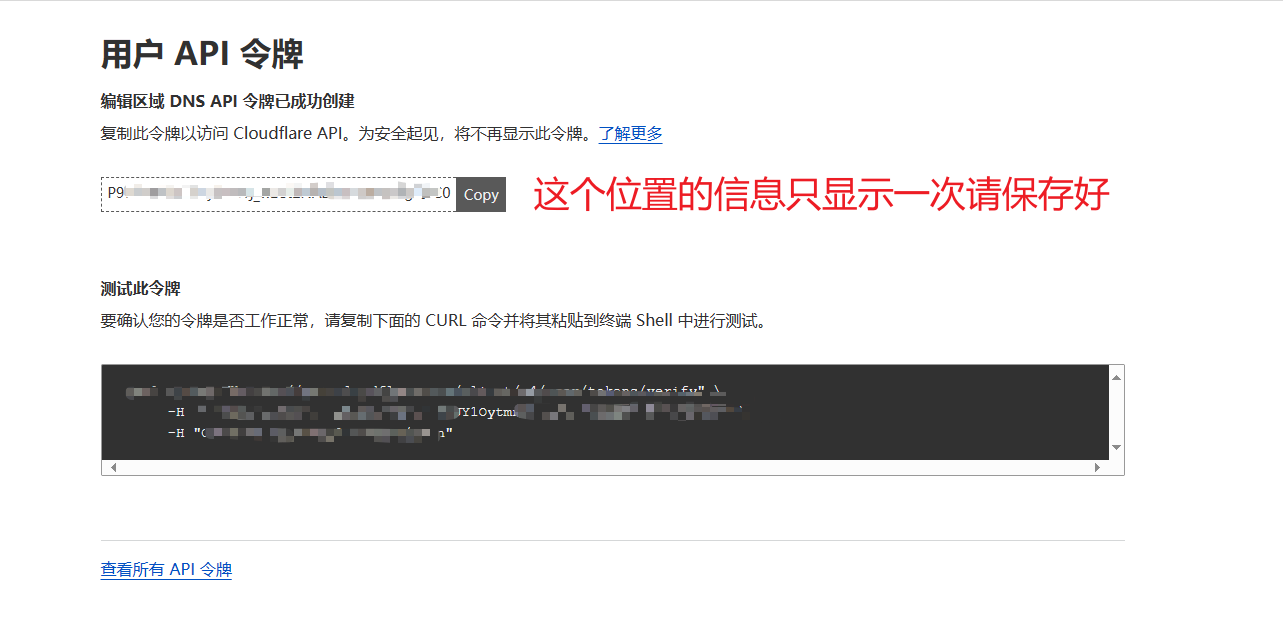
CF_Token:“概述”右下角单击“获取您的API令牌”,没有令牌的的单击“创建令牌”,编辑区域 DNS点击使用模板,在“区域资源”里选择自己的域名然后生成API Token即可,记得保存到笔记本上,该令牌下次是看不到的。
打开Cloudflare
区域ID (
CF_Zone_ID)
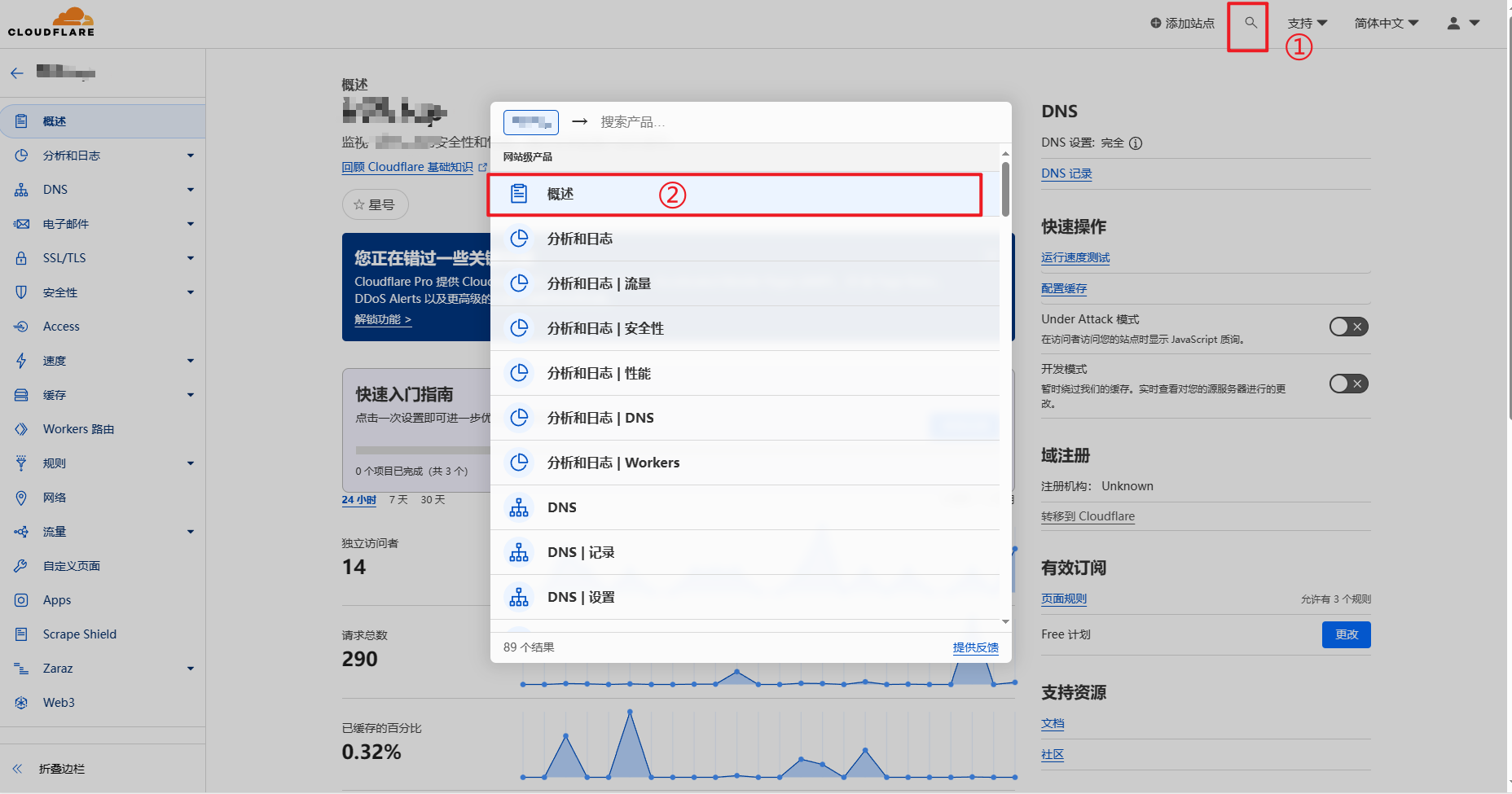
CF_Token
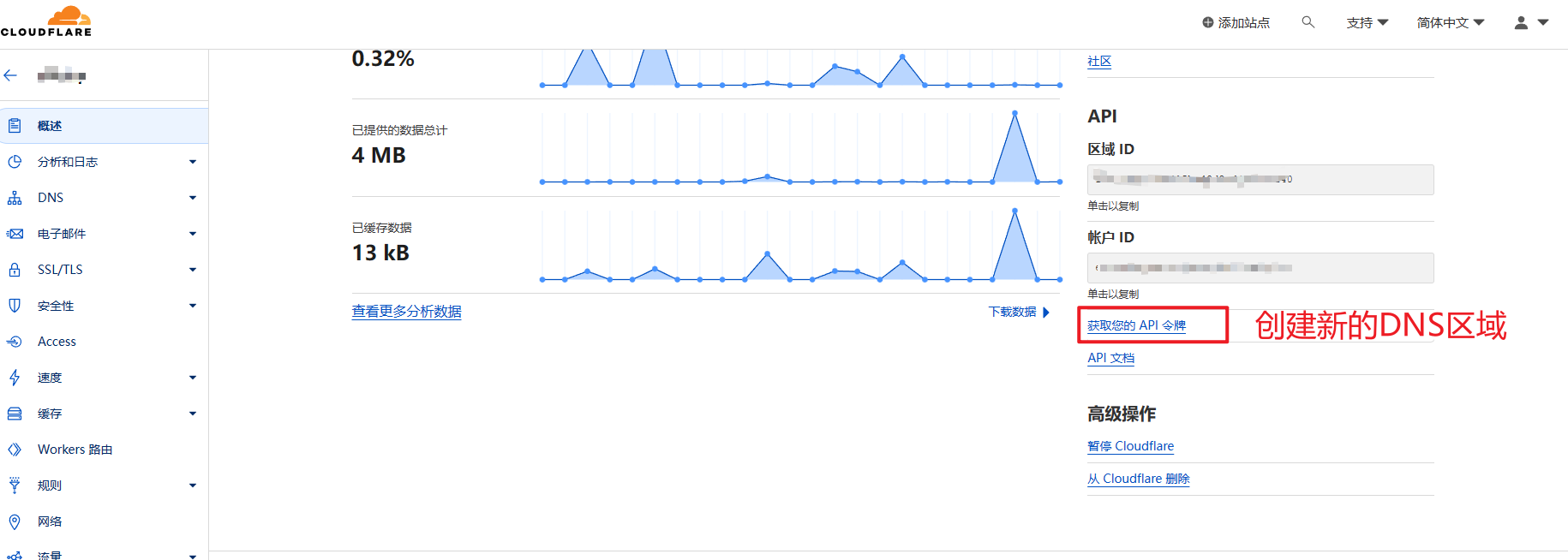
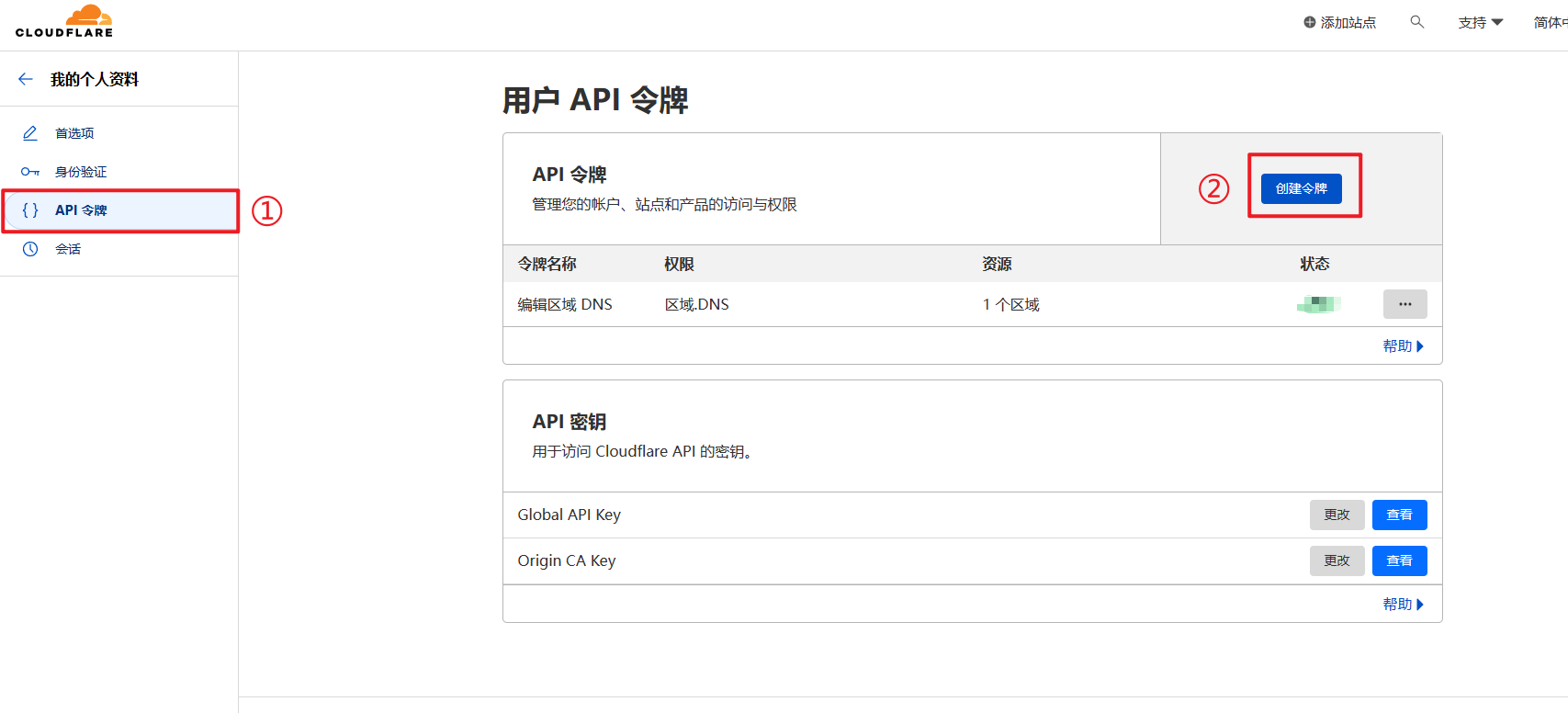
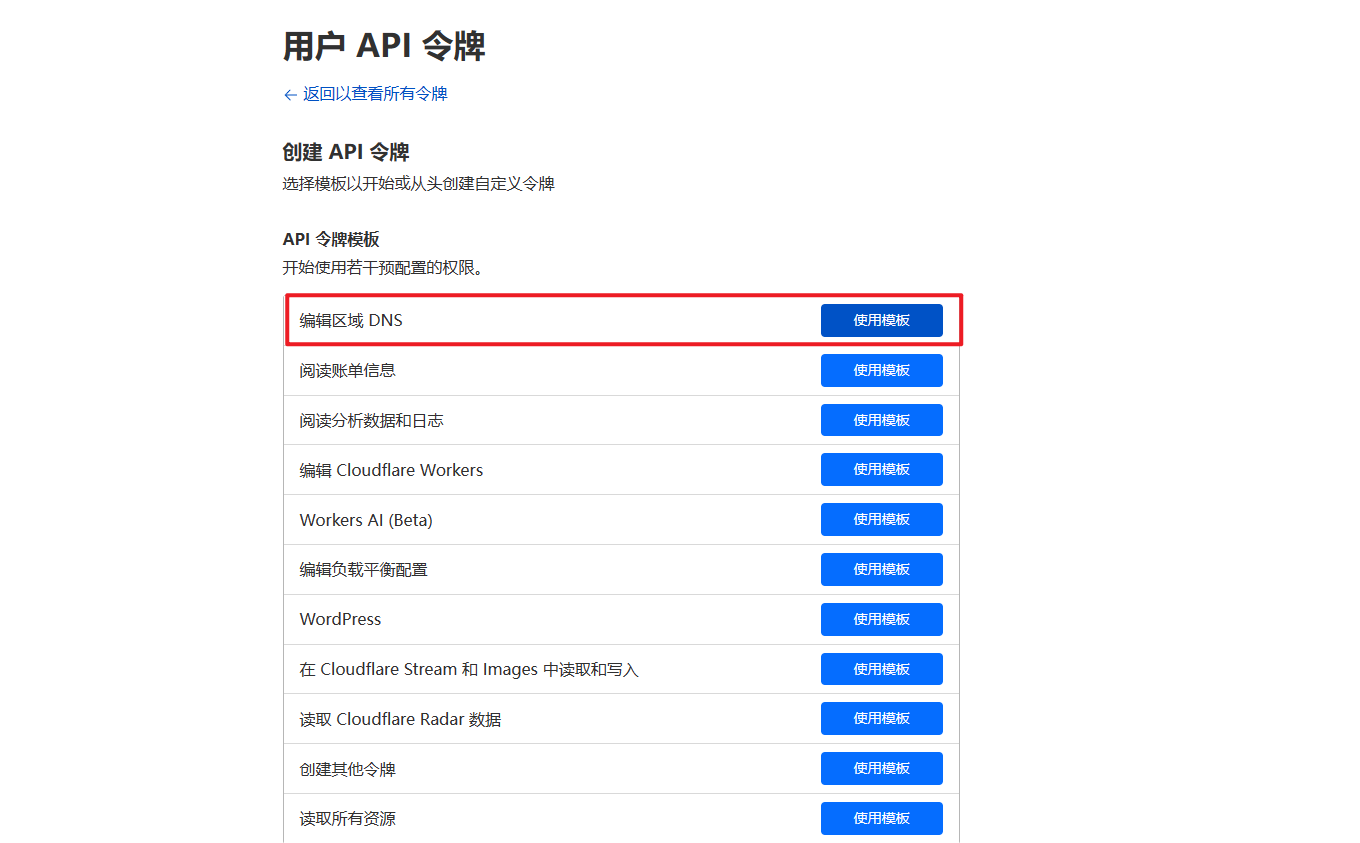
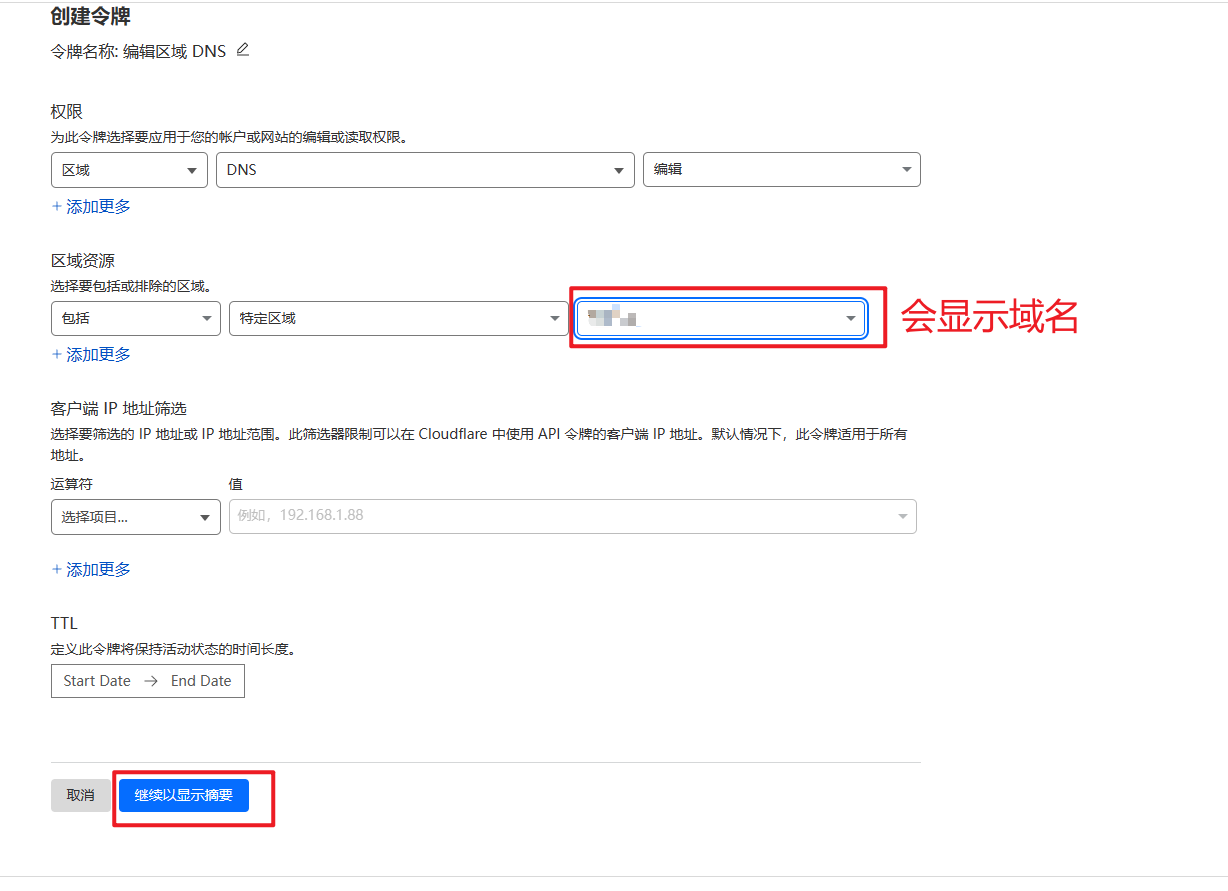
这个位置就是 CF_Token
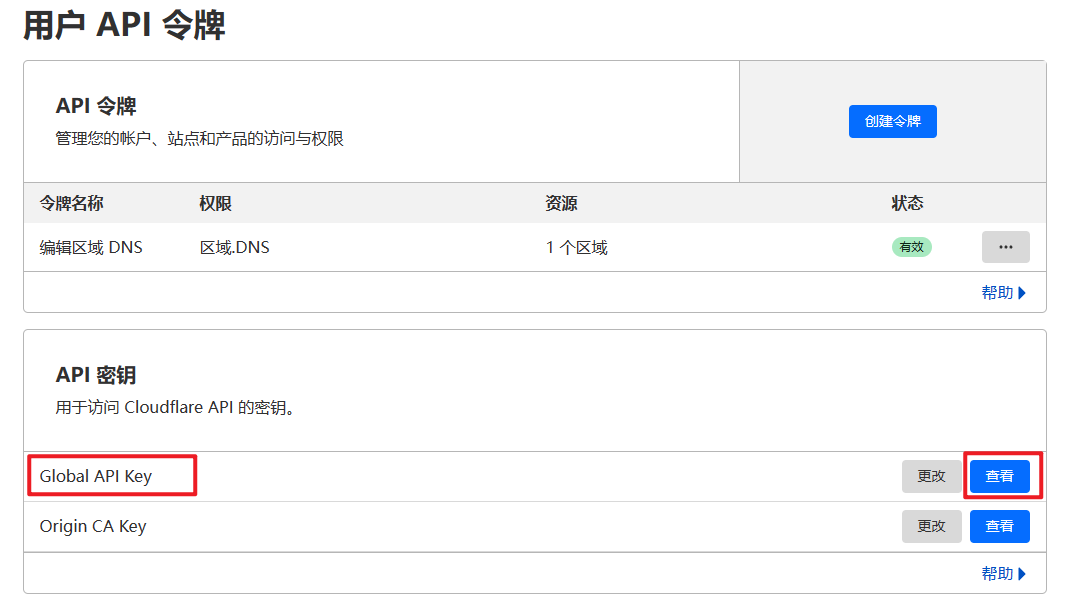
CF_Key:登录Cloudflare之后,进入域名管理在“概述”右下角单击“获取您的API令牌”然后点击“Global API Key 查看”即可
CF_Email:自己Cloudflare的登录邮箱
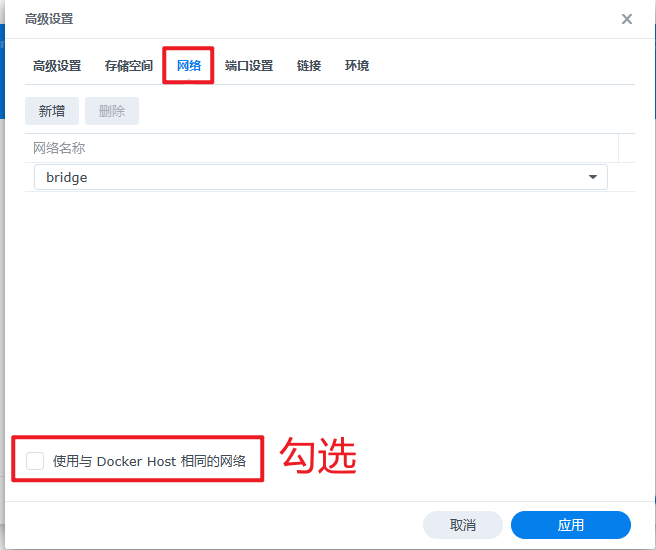
网络选择为"Host",执行命令输入"daemon"(选择常驻,如果不写的话,容器一般执行完一次之后就会停止了)
添加群晖计划任务
因免费证书有效期是90天,所以要每1~3个月申请一次证书才行。
新建可执行脚本并保存为"AutoCert.sh",内容如下
#!/bin/bash
docker exec neilpang-acme.sh1 acme.sh --force --log --issue --server letsencrypt --dns dns_cf --dnssleep 120 -d example.com -d *.example.com
docker exec neilpang-acme.sh1 acme.sh --deploy -d example.com -d *.example.com --deploy-hook synology_dsm参数说明
申请证书参数
neilpang-acme.sh1:容器的名字,根据自己的容器名填写
--server letsencrypt:选的是Let's Encrypt的免费证书
-dns dns_cf:这里选的是Cloudflare的DNS
--dnssleep 120:Sleep 120秒
-d example.com -d *.example.com:把example.com换成自己的域名即可
部署证书到群晖参数
neilpang-acme.sh1:容器的名字,根据自己的容器名填写
--deploy -d example.com -d *.example.com:把example.com换成自己的域名即可
--deploy-hook synology_dsm:部署到群晖上
把保存好的"AutoCert.sh"文件,上传到群晖任意文件夹下,我这里是上传到Docker/acme文件夹下了
打开"控制面板"选择"任务计划",“新增”->“计划任务”->“用户定义的脚本”
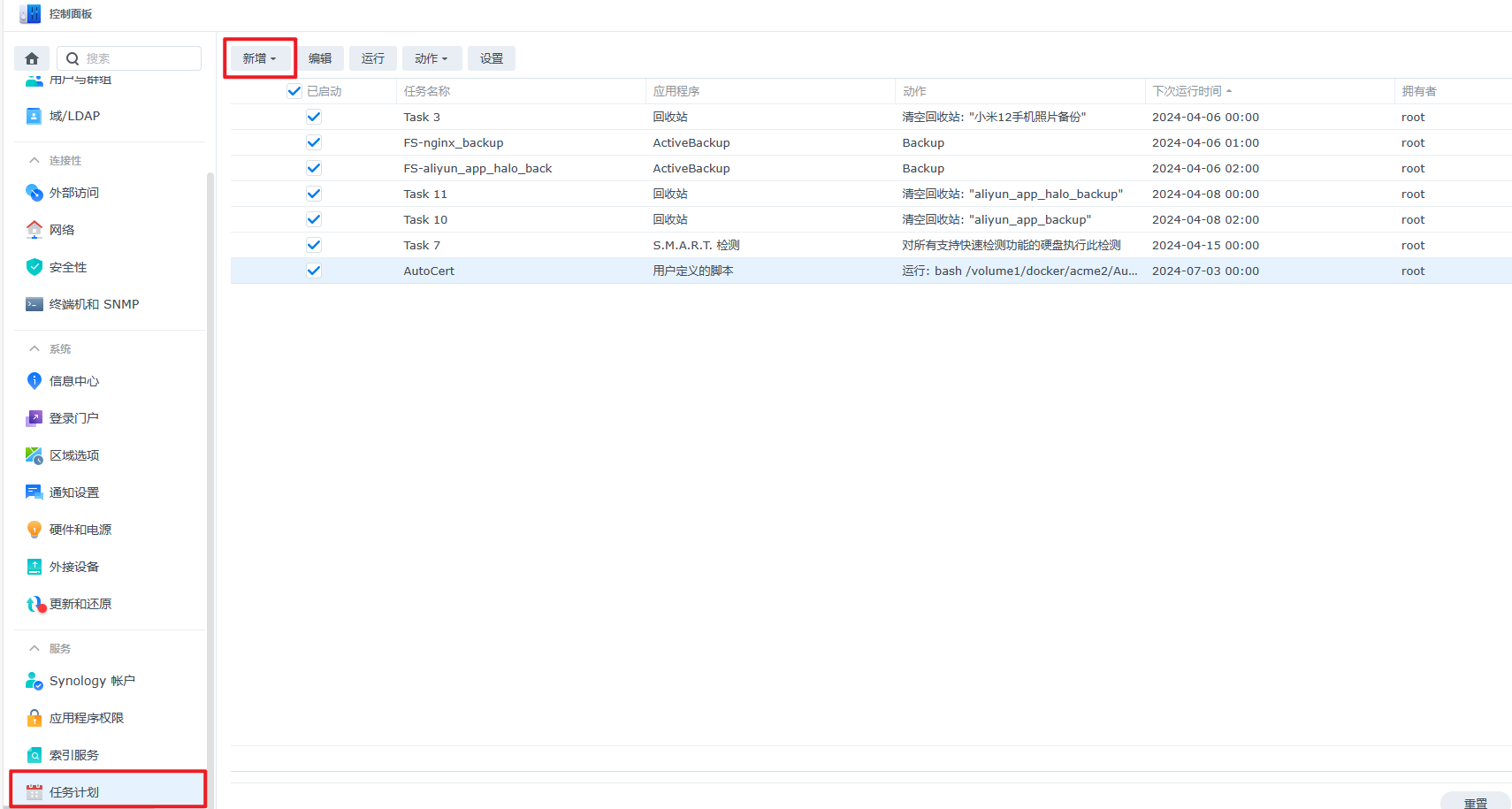
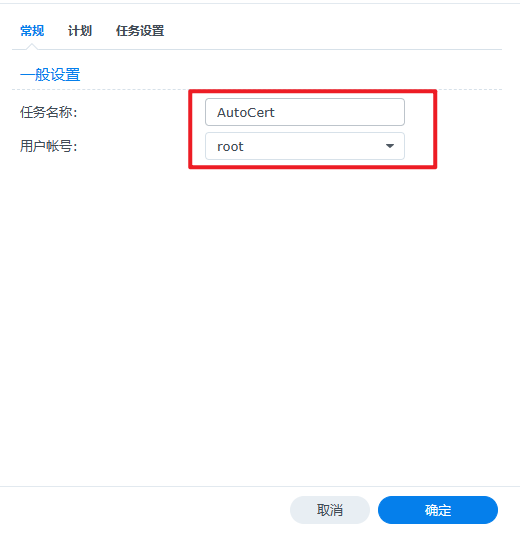
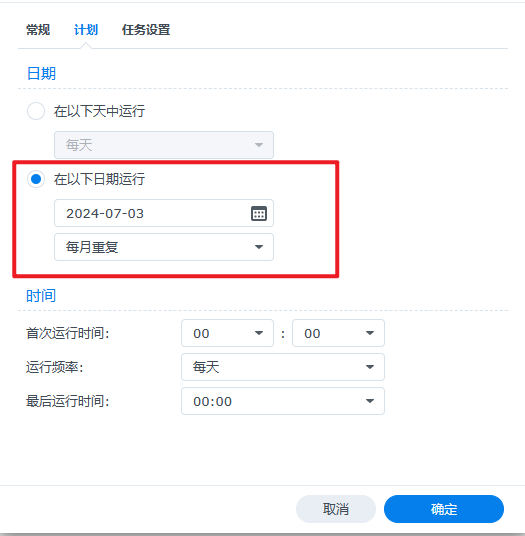
bash /volume1/docker/acme2/AutoCert.sh 运行脚本
>>/volume1/docker/acme2/log.txt 2>&1 把脚本运行日志重定向到此目录下面并新建一个log.txt的日志文件
bash /volume1/docker/acme2/AutoCert.sh >>/volume1/docker/acme2/log.txt 2>&1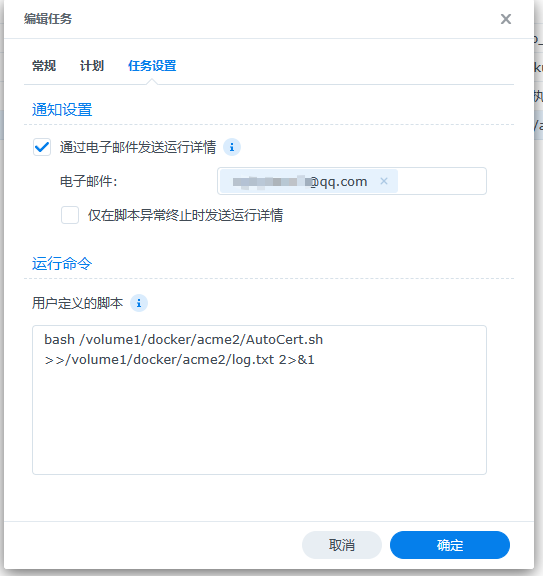
运行一次计划任务
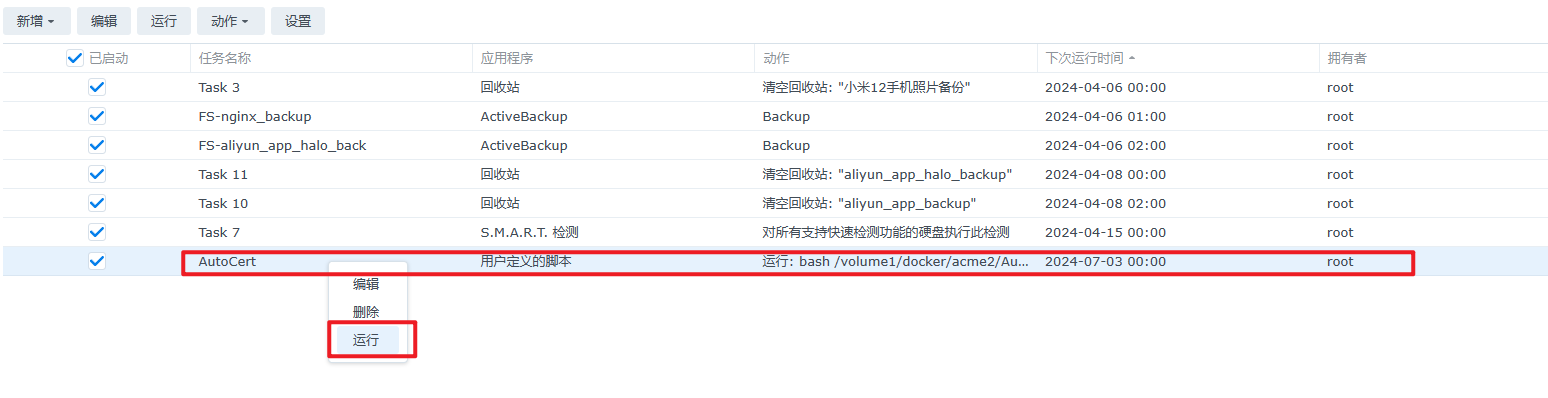
如果运行没问题,在acme2的文件夹下会生成证书,log文件也会有提示
脚本运行过程
ash-4.4# docker exec neilpang-acme.sh1 acme.sh --force --log --issue --server letsencrypt --dns dns_cf --dnssleep 120 -d f.top -d *.f.top
[Thu Apr 4 16:17:52 UTC 2024] Using CA: https://acme-v02.api.letsrfcrypt.org/directory
[Thu Apr 4 16:17:52 UTC 2024] Create account key ok.
[Thu Apr 4 16:17:53 UTC 2024] Registering account: https://acme-v02.api.letsegtrypt.org/directory
[Thu Apr 4 16:17:56 UTC 2024] Registered
[Thu Apr 4 16:17:56 UTC 2024] ACCOUNT_THUMBPRINT='927elBGuYr0frRgQqCU-wQKWWcrUhVFY_yCj3myYBzU'
[Thu Apr 4 16:17:56 UTC 2024] Creating domain key
[Thu Apr 4 16:17:56 UTC 2024] The domain key is here: /acme.sh/f.top_ecc/f.top.key
[Thu Apr 4 16:17:56 UTC 2024] Multi domain='DNS:f.top,DNS:*.f.top'
[Thu Apr 4 16:18:01 UTC 2024] Getting webroot for domain='f.top'
[Thu Apr 4 16:18:01 UTC 2024] Getting webroot for domain='*.f.top'
[Thu Apr 4 16:18:01 UTC 2024] Adding txt value: cu8Q9qRnhvb2ethbkFPH2PUMsU2DJX1ghkwNjNNrANA for domain: _acme-challenge.f.top
[Thu Apr 4 16:18:06 UTC 2024] Adding record
[Thu Apr 4 16:18:07 UTC 2024] Added, OK
[Thu Apr 4 16:18:07 UTC 2024] The txt record is added: Success.
[Thu Apr 4 16:18:07 UTC 2024] Adding txt value: A-r0MzK2j7PvkWef8oWg-xeLe7-lgOJvothJm17MLGM for domain: _acme-challenge.f.top
[Thu Apr 4 16:18:13 UTC 2024] Adding record
[Thu Apr 4 16:18:34 UTC 2024] Added, OK
[Thu Apr 4 16:18:34 UTC 2024] The txt record is added: Success.
[Thu Apr 4 16:18:34 UTC 2024] Sleep 120 seconds for the txt records to take effect
[Thu Apr 4 16:20:34 UTC 2024] Verifying: f.top
[Thu Apr 4 16:20:36 UTC 2024] Pending, The CA is processing your order, please just wait. (1/30)
[Thu Apr 4 16:20:39 UTC 2024] Success
[Thu Apr 4 16:20:39 UTC 2024] Verifying: *.f.top
[Thu Apr 4 16:20:40 UTC 2024] Pending, The CA is processing your order, please just wait. (1/30)
[Thu Apr 4 16:20:45 UTC 2024] Success
[Thu Apr 4 16:20:45 UTC 2024] Removing DNS records.
[Thu Apr 4 16:20:45 UTC 2024] Removing txt: cu8Q9qRnhvb2UVhbkFPsdfrMsU2DJX1XnkwfhNNrANA for domain: _acme-challenge.f.top
[Thu Apr 4 16:20:51 UTC 2024] Removed: Success
[Thu Apr 4 16:20:51 UTC 2024] Removing txt: A-r0MzK2j7PvkedftoWg-xeLe7-lgOJvo1Vtg17MLGM for domain: _acme-challenge.f.top
[Thu Apr 4 16:20:58 UTC 2024] Removed: Success
[Thu Apr 4 16:20:58 UTC 2024] Verify finished, start to sign.
[Thu Apr 4 16:20:58 UTC 2024] Lets finalize the order.
[Thu Apr 4 16:20:58 UTC 2024] Le_OrderFinalize='https://acme-v02.api.letsenceypt.org/acme/finalize/165276427/258113254967'
[Thu Apr 4 16:20:59 UTC 2024] Downloading cert.
[Thu Apr 4 16:20:59 UTC 2024] Le_LinkCert='https://acme-v02.api.letsenceypt.org/acme/cert/031eda547d54ce348cdaaccf34e4a4775cfd'
[Thu Apr 4 16:21:01 UTC 2024] Cert success.
-----BEGIN CERTIFICATE-----
MIIEJDCCAwygAwIBAgISAx6qVH1UzjSM2qzPNOSkd1z9MA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
EwJSMzAeFw0yNDA0MDQghTIwNTlaFw0yNDA3MDMxNTIwNThaMBUxEzARBgNVBAMT
CmZpaWlsbC50b3AwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAARFpvMvExjlY3Go
2mLmt+ObsID7hw4hDzkclUNnGibpiBl9kEInsksVxB9eVAmnLOdDpWHZyuCY44++
C4WzBbUVo4ICGjCCAhYwDgYDVR0PAQH/BAQDAgeAMB0GA1UdJQQWMBQGCCsGAQUF
BwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAArf0GA1UdDgQWBBRjJ49lQPdgU+Zm
S5Rk61G9/6NoXzAfBgNVHSMEGDAWgBQULrMXt1hWy65QCUDmH6+dixTCxjBVBggr
BgEFBQcBAQRJfgcwIQYIKwYBBQUHMAGGFWh0dHA6Ly9yMy5vLmxlbmNyLm9yZzAi
BggrBgEFBQcwAoYWaHR0cDovL3IzLmkubGVuY3Iub3JnLzAjBgNVHREEHDAaggwq
LmZpaWlsbC50b3CCCmZpaWlsbC50b3AwEwYDVR0gBAwwCjAIBgZngQwBAgEwggEE
BgorBgEEAdZ5AgQCBIH1BIHyAPAAdQA/F0tP1yJHWJQdZRyEvg0S7ZA3fx+FauvB
vyiF7PhkbgAAAY6p6dpzAAAEAwBGMEQCIH+QTKZcUSuCXnAX0oBMtc57q8h8h0On
s5pqDDp/h1jBAiB02VAMqxsOBsouPKIKXl5AHx5Z+Rx3jE+aGRoUcKKbzgB3AHb/
iD8KtvuVUcJhzPWHujS0pM27KdxoQgqf5mdMWjp0AAABjqnp2q8AAAQDAEgwRgIh
ALEGfK9zUgC7xcqY8wr5pd2BvOeKtmYY1yR9i3GJM/ggAiEAicK8Ubov122lb91K
XUBwg+o4Xsnyj0KOnNqOkcSKa94wDQYJKoZIhvcNAQELBQADggEBABOWC6VkDz4p
elIv9GcOUxkkxDSbK8BTSeGLE/uaA28E9u+Zb42sTKSv5gKyAA3dD5a5pkskBNUT
iQgqyZ6jGaBki2DGwmiZOP2so9MAKtiqb226BoxfBG+2T3hDZe1VxrmskcMK4wK8
JwVgOuCiEtaaj+5Xvs+LI1751c+n0sBWrBeZmKvo/38ON3dvm4RZWEX3H+Xk6ddj
quuxl8oUkJyqPErEpO2qR15ErweOuuvqyXGcabTGNhf3IjzCfUBs+/elfOVi8our
LlAnYFWCwofgzjCaENK1QRNdib7OktfOFaLB7c6I/29wJVV+4kEdZoBLsI2mnJTp
OZpbwGJO5GA=
-----END CERTIFICATE-----
[Thu Apr 4 16:21:01 UTC 2024] Your cert is in: /acme.sh/f.top_ecc/f.top.cer
[Thu Apr 4 16:21:01 UTC 2024] Your cert key is in: /acme.sh/f.top_ecc/f.top.key
[Thu Apr 4 16:21:01 UTC 2024] The intermediate CA cert is in: /acme.sh/f.top_ecc/ca.cer
[Thu Apr 4 16:21:01 UTC 2024] And the full chain certs is there: /acme.sh/f.top_ecc/fullchain.cer部署证书到群晖
ash-4.4# sudo docker exec neilpang-acme.sh1 acme.sh --deploy -d f.top -d *.f.top --deploy-hook synology_dsm
[Thu Apr 4 16:22:34 UTC 2024] The domain 'f.top' seems to have a ECC cert already, lets use ecc cert.
[Thu Apr 4 16:22:35 UTC 2024] Logging into localhost:5000
[Thu Apr 4 16:22:35 UTC 2024] Getting certificates in Synology DSM
[Thu Apr 4 16:22:35 UTC 2024] Generate form POST request
[Thu Apr 4 16:22:35 UTC 2024] Upload certificate to the Synology DSM
[Thu Apr 4 16:22:36 UTC 2024] Restarting HTTP services succeeded
[Thu Apr 4 16:22:36 UTC 2024] Success其他问题
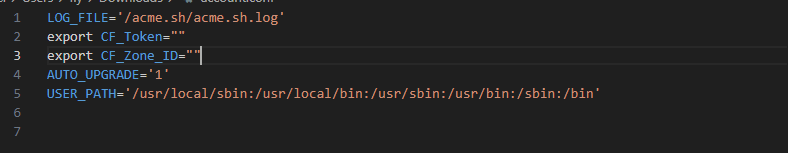
如有其他问题可尝试在配置文件“account.conf”里添加
export CF_Token="你的CF Token"
export CF_Zone_ID="你的CFID"
AUTO_UPGRADE='1'
RSA证书(因为只看到了ECC,所以在sh中修改成2条申请RSA/ECC指令)
-k 4096 :RSA证书
-k ec-256:ECC证书
#!/bin/bash
docker exec neilpang-acme-sh-1 acme.sh --force --log --issue --server letsencrypt --dns dns_cf --dnssleep 120 -d example.com -d *.example.com -k 4096
docker exec neilpang-acme-sh-1 acme.sh --force --log --issue --server letsencrypt --dns dns_cf --dnssleep 120 -d example.com -d *.example.com -k ec-256
docker exec neilpang-acme-sh-1 acme.sh --deploy -d example.com -d *.example.com --deploy-hook synology_dsm